HILLARY CLINTON CONTROLS 50,000 FBI ENCRYPTION KEYS—PROVES MUELLER’S WITCH HUNT IS TREASONOUS
by Americans for Innovation
With these encryption keys, nothing in our digital lives is off limits to the Clinton’s and their conspirators
President Trump’s new executive order can be sabotaged with these keys; alternatively, he can use the order to prosecute these criminals
Many foreign powers have conspired with the SES and their Queen’s Privy Council overlords since before 1993

AFI (Nov. 06, 2015). Complicit encryption geeks enable the American spy state. Americans for Innovation.
AFI (Nov. 25, 2015). Dell and Lenovo (IBM) ship computers with spy state backdoors. Americans for Innovation.
http://youtu.be/-zWWJ1BzKgI | (Raw *.mp4 video file—use if the YouTube version is censored).
SPECIAL NOTICE: This post is a work in progress. You are encouraged to return to pick up additional evidence as it is added. Indictable evidence continues to pour in for use by prosecutors, alternative media, Treasury, U.S. Marshalls and military tribunals. These criminals have relied on the fact that encryption, cryptography and cryptanalysis is a field of esoteric mathematics for which the average person has little interest. Hopefully, that will now change.
Cryptography—the use of codes and ciphers to protect secrets—began thousands of years ago. Until recent decades, it has been the story of what might be called classic cryptography — that is, of methods of encryption that use pen and paper, or perhaps simple mechanical aids. In the early 20th century, the invention of complex mechanical and electromechanical machines, such as the Enigma rotor machine, provided more sophisticated and efficient means of encryption; and the subsequent introduction of electronics and computing has allowed elaborate schemes of still greater complexity, most of which are entirely unsuited to pen and paper.
In a simple form, simply scrambling the letters in a word is a basic form of cryptography. HELLO might become OLHEL or LEHLO. In more sophisticated approaches, look up tables contain readable words in the first column and a replacement word in the second. The resulting message looks like jibberish until the look up table is used by the recipient. The public key infrastructure and certificate authorities discussed in this post are simply more scrambled forms of encryption.
The earliest example known was from an Egyptian scribe about 1900 BC. Assyrian merchants used a form of encryption called intaglio in 1500 BC. Hebrew scribes wrote a copy of the Book of Jeremiah in a substitution cipher in 605 BC. In 487 BC the Greeks used a “skytale” to encrypt important messages. Julius Caesar (100-44 BC) encrypted government communications. Abu ‘ Abd al-Rahman al-Khalil ibn Ahmad ibn Amr ibn Tammam al Farahidi al-Zadi al Yahmadi wrote a book on cryptography in 725-790 AD. Thomas Jefferson invented a wheel cipher. Tellingly, a design in 1976 by IBM based on “the Lucifer cipher” is now used and called “triple-DES” (the Triple Data Encryption Algorithm).
When the German Enigma Machine was cracked in World War II, the Allies could read ALL German communications from that point forward. In the same way, Hillary’s access to the PKI, Dual_EC_DRBG algorithm and Certificate Authorities gives her access to The Internet of Things’ version of the Enigma Machine break, which was considered by western Supreme Allied Commander Dwight D. Eisenhower to have been “decisive” to the Allied victory. See History of Encryption.
(SEP. 16, 2018)—Imagine that your identity is stolen suddenly.
Your healthcare, education, police, employment and bank records are all altered overnight to make you look like an embezzler. Imagine you are jolted awake the following morning by the police bashing in your door to arrest you. Imagine that the local TV is already carrying news of your arrest using a drunken party photo of you off your phone.
Imagine further that you are Hillary Clinton. You need for 55,000 Clinton Foundation emails on FBI director James Comey computer to disappear. Poof. They’re wiped without a trace.
Imagine still further that you are Lord Mark Malloch-Brown from the Queen’s Privy Council. You need to erase the U.S. Department of Treasury’s new evidence of foreign meddling embedded in your Smartmatic voting machines. Your bunk buddy George Soros makes a call to Hillary. Poof. This evidence is digitally wiped, without a trace.
This cannot happen in America you say? Think again.
Since these people have full backdoor access to any computer or phone on the Internet, can they ever be caught? Yes, once we realize how they do it. That method has just been discovered.
Truth is, Hillary Clinton literally has access to every computer on the Internet through a company named ENTRUST. Her 19-year Rose Law Firm partner Jerry C. Jones directs the company (now ostensibly run by a Silicon Valley dude named Orlando Bravo and his private equity firm Thoma Bravo, LLC), and has done since Dec. 2003. Entrust issues the encryption keys for most major governments and companies in the world.
WHAT IS AN ENCRYPTION KEY WHY IS THIS DISCOVERY SO DEVASTATING TO THE DEEP STATE SHADOW GOVERNMENT?
Put simply, encryption keys are used on both the sender’s and receiver’s computers to send data. It takes two keys to make a connection to send or receive data. The Clinton Administration created “trusted Certificate Authorities (CA)” to check with to make sure that the two keys are the real sender and receiver. If your keys are not approved by the CA, your connection will be blocked. In the hands of tyrannical globalists like Hillary Clinton, Barack Obama, George Soros, Eric Schmidt and Robert Mueller, this will be the new censorship on the Internet.
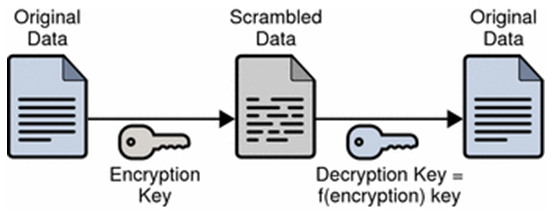
Encryption scrambles the contents of your messages then files and unscrambles them once they reach their intended destinations using digital keys managed by encryption engineers.
For example, the phrase “your cancer treatment program” would be encrypted with a digital key and travel through the Internet as “Qij\aq6NB5Lf@;kndFq7CN{Q{.” So, even if it was intercepted it could not be read. The theory is that this knowledge of your medical condition would remain confidential between you and your doctor. Not so for Hillary, she would see you have cancer and could use that information for blackmail, extortion or murder, whatever worked for her.
These CA’s make a big deal in their propaganda that you can “trust” them not to use or spoof your identity to get access to data that you and they are not authorized to have. That is a boldface lie. No wonder these people have the countenances of criminals. They are, and they know it.
Suppose you are the CA who issues keys to the FBI. Suppose you want to see the evidence being gathered against you in an investigation.
All you have to do is “borrow” the FBI key from Hillary or ENTRUST. Then you can connect to the target FBI computer using a bogus key created for you by ENTRUST, and voile! You then have two “trusted” keys so the FBI computers let you in. There are technical nuances to this description, but basically, you can do what you want with these keys. Don’t let trollers try to baffle you with techno-jargon to throw your dogs off the scent. Lucifer(literally, IBM Triple-DES) is in these encryption details.
Hillary Clinton has this level of access to practically all data on the planet, including the FBI, NSA, Departments of State, Commerce, Energy, Treasury, GSA, Patent Office, Post Office, NIST, as well as numerous foreign government and commercial entities. See ENTRUST 10-K Annual Reports (1998-2009). SEC Edgar.
Now that we finally know how the Clinton’s stay one step ahead of the sheriff, we can now stop them.
MORE HARD PROOF THAT HILLARY CLINTON IS A DIGITAL MONSTER
In this post, we will prove without a doubt how Hillary Clinton cleverly wormed her way into full access and control for 50,000 FBI encryption keys.
They are likely managing this empire from Obama’s Google-constructed U.S. Digital Service bunker three blocks from the White House manned by Valerie Jarrett and Eric Holder.
We admit that these findings sound more like Grisham fiction. But the evidence is a pesky thing. The evidence is now pouring out.
THE EVIDENCE PROVIDED IS “JUDICIALLY RECOGNIZABLE” AND INDICTABLE, WE BELIEVE
“Notoriously public” information, like the U.S. Securities & Exchange Commission filings that we cite, is evidence that requires no further verification to be used in litigation, hence the adjective “notoriously.” This means that the information is so publicly noteworthy that further proof of validity is unnecessary. For example, John F. Kennedy was assassinated in 1973. That is a notoriously public fact and no proof is needed.
Notoriously public facts, like SEC filings, are “judicially recognizable” and can be accepted as truthful since the submitter attests to the SEC that they are true. It is criminal fraud to lie intentionally in SEC filings.
TIMELINE: BILL & HILLARY CLINTON BEGAN ORCHESTRATING UNFETTERED ACCESS TO THE FBI’S ENCRYPTION KEYS IN 1993
On Jun. 07, 1993, the new Clinton Administration convened the “Third CPSR Cryptography and Privacy Conference (CPSR – Computer Professionals For Social Responsibility).”
The conference was held two days before an important Jun. 09, 1993 House hearing on “encryption and telecommunications network security.” The conference gathered over 106 attendees representing government, politics, commerce, manufacturing, industry, media, technology, telecommunications, healthcare, banking, education, faith and accounting. That’s plenty of arm-twisting, even for Washington, D.C.
The meeting sponsor was globalist advocate Carnegie Endowment for International Peace.
The hosts included:
(1) James P. Chandler, III, George Washington University intellectual property and national security law professor, and later patent attorney for social networking inventor Leader Technologies, Inc. (Jan. 2000);
2) John D. Podesta, chief of staff and campaign manager to Bill Clinton, Barack Obama and Hillary Clinton;
(3) Stephen D. Crocker, founding member of the illegal public-private conspiracy group Highland’s Forum/Group (Feb. 1995), then Barack Obama’s director of ICANN (Internet Corporation for Assigned Names and Numbers) who ceded control to the UN on Oct. 01, 2016—one month before Donald J. Trump was elected president.
HILLARY HID THE 1993 ENCRYPTION MEETING ATTENDEE LIST
The information about this meeting was hidden on Hillary’s private email server. It was unearthed by corruption watchdog Judicial Watch after they pressed the State Department in court to release the document.
Continue reading at: http://americans4innovation.blogspot.com/2018/09/hillary-clinton-controls-50000-fbi_15.html

