BIG BROTHER IS WATCHING YOU — FOR REAL
“THE CONSCIOUS AND INTELLIGENT MANIPULATION OF THE ORGANIZED HABITS AND OPINIONS OF THE MASSES IS AN IMPORTANT ELEMENT IN DEMOCRATIC SOCIETY. THOSE WHO MANIPULATE THIS UNSEEN MECHANISM OF SOCIETY CONSTITUTE AN INVISIBLE GOVERNMENT WHICH IS THE TRUE RULING POWER OF OUR COUNTRY.” EDWARD BERNAYS, PROPAGANDA
There really is an information war, and you are right in the middle of the battlefield. Are you ready?
Sure, we are being surveilled, watched, listened to, wiretapped, and subliminally messaged – but what do I care as long as I have the Internet of Things to do my regal bidding?
Your every move, query, keystroke, like, phone call, message, and digital choice is creating your own personalized “dark profile” that can be used against you not only for commercial purposes but to literally program your thinking.
Once your “dark profile” is created, it can be used against you to manipulate your life in ways that are unimaginable, intervening in finances, work, social life, and the political realm simultaneously.
Government documents admit to heinous “digital crimes” against all Americans with 100% surveillance through all “devices” with microchip processors.
You are more than just being “watched”; your very thoughts (neural networks) are being manipulated.
It is each internet user’s duty to learn about these cyber-programs of manipulation and to be on guard! Ignorance and apathy will not protect you.
The Anonymous Patriots have been asked to recap the methods that broadcasters use to control people through televisions, radios, cell phones, and computers. We have written prior Citizens’ Intelligence Reports on these important topics. Here, we update and refresh our intelligence report on the many weapons that are being used to “dumb” people down enough to accept political, military, and corporate propaganda without questioning the nonsense, lies, and post-truth politics that spew forth from every propaganda, corporate, main stream media outlet.
Warning: Do not read this article if you are not ready to confront evil in some of its very ugly forms. The military/corporate warlords are engaged in a battle to steal your willpower, your hard-earned income, and your political opinion. They want to turn them into never-ending commercialism, banal and immoral entertainment, and post-truth politics that are frankly not believable without the subliminal messaging and overt mind-control.
They are attempting to control human thinking until “free thoughts” are wiped-out. The cyber-war is actually a fight for control of your soul and spirit, and the weapons being used against us are in our very own hands at the end of our fingertips, and in our home, workplace, and environment, blaring from every television, computer, and radio.
We must learn the methods of our enemies so that their tricks, scams, and mental manipulation can have no power over our soul and spirit and the human right to have “free thought” without being controlled by the overlords of technology.
READY OR NOT – THE BATTLE HAS BEGUN
A new technological revolution is taking place and each person on the internet will be affected. Many will fall prey to this information weapon that will be used against us to  control our lives. For those on social media like Facebook, or those that have bought into using the Internet of Things, your life is about to change radically as you believe you are becoming more “free” by the machines that serve you, when in fact, you have willingly become imprisoned through the internet.
control our lives. For those on social media like Facebook, or those that have bought into using the Internet of Things, your life is about to change radically as you believe you are becoming more “free” by the machines that serve you, when in fact, you have willingly become imprisoned through the internet.
The more you participate in the automatic information fed directly to your machines that have personalized your news, entertainment, business, and “life-patterns”, the more you will think you are free and fully informed. But in fact, you will be limited by what your pattern-of-life generates as your individualized algorithms as a mechanical virtual world which will be created around you and becomes your personalized “digital prison” that you happily accept because it seems like a digital heaven to you.
Have you been lolled into dreaming sleep yet? You will be.
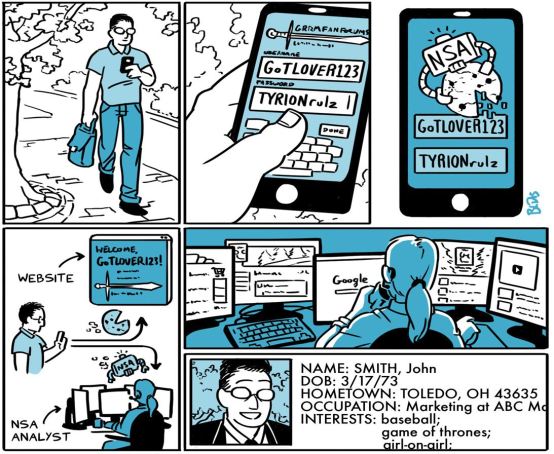
Your new digital prison is being created for you every time you do an internet search, click a like button on Facebook, type a word into your computer, choose something to watch on TV, or even speak a word into your phone. Every speck of “information” that you participate in is used to make your personalized digital life-pattern profile – your “dark profile.”
Even your bank account and everything you spend a digital penny on is being gathered in an NSA program called Marina that knows so much about you that when you get into your car on a day you have a weekly appointment, your phone “pings” in the route and distance to your destination automatically.
Your phone can also activate the controls of all your devices that can be connected to the Internet of Things. As you approach your house with your phone, your garage door opens automatically as the lights in the house come on and the house alarm is turned off while your coffee maker brews a coffee and your TV comes on to your usual show as the heating pad in your easy chair turns on to your favorite setting. There is no end to the “machine intelligence” support you can get from mechanically augmented reality.
 Not enough for you? Then put on your 3-D visor and enter your self-created virtual reality world where it feels you are free to do as you please – seemingly, a type of virtual freedom.
Not enough for you? Then put on your 3-D visor and enter your self-created virtual reality world where it feels you are free to do as you please – seemingly, a type of virtual freedom.
Can you see where this is going in the future? The future is here today because all the things just described have already been created and are ready to be offered to every American with an internet connection and the money to upgrade to the new Google called Alphabet. Eric Schimdt, the CEO of Alphabet has bragged about this new system that he says is ready to go.
Whether you know it or not, what is described above is already happening on a commercial level and soon will escalate to an overt military level while the innocent internet user is lulled into believing that they are simply having fun. Since most American businesses have some component on the internet, the military weaponization of the internet may be as powerful as the threat of global nuclear annihilation.
Just imagine if the internet were turned off tomorrow for good – permanently, never to return. Most of what we think of as modern life would end and many people would never recover. Economies would collapse, wars would rage, and children wouldn’t know what to do or what to think.
MODERN LIFE WOULD COLLAPSE BECAUSE THE WEAPON OF THE INTERNET ALREADY HAS CONTROL OF MODERN LIFE.
We need to see the internet and its “wonders” for exactly what they are – weapons of mass social manipulation. When we can see the evil plans of those who have advanced this technology without the moral compass necessary to guide such powerful tools, then perhaps we can change these innovations from weapons into the information tools we initially believed they were intended to be. Information was supposed to free humanity, not imprison it in a virtual world where education is replaced by entertainment, religion is replaced by consumerism, and the real world in replaced by virtual reality.
WEAPONIZATION OF THE INTERNET
Taxpayers of the United States, through the CIA’s advanced research and development company In-Q-Tel, funded the open source program that became Facebook, Google, Intel, Apple, and Microsoft. These companies have weaponized these devices and systems against the citizens of the world.
Once the Silicon Valley high-tech “dummy” companies are established by stooges chosen for their willingness to incorporate military “back doors” into all their products, the NSA/CIA/FBI uses the information gleaned from those companies to surveil every American through every devise that broadcasts a signal – cell phone, computer, television, or any devise on the Internet of Things.
Intelligence agencies can simply type in a query and access the metadata collected from every digital devise on the internet or that uses wi-fi or cell phone towers. This information is then used to target individuals for consumerism and/or U.S. Department of Defense intelligence collection. If an internet user is targeted, there are hundreds of ways to attack the user and manipulate his/her buying habits, personal life-pattern choices, and even the way the user thinks.
The object of the intelligence is simply to control the user. Social networks on the internet are military experiments in social manipulation, what the military calls PSYOPS – or psychological operations.
One of the NSA programs used to gather the Internet metadata is XKeyscore, a secret computer system first used by the National Security Agency (NSA) for searching and analyzing global Internet data, which it collects on a daily basis.
It enables almost unlimited surveillance of anyone anywhere in the world. The NSA’s databank of collected communications allows its analysts to listen to the calls or read the emails of everything that the NSA has stored, or look at the browsing histories or Google search terms that you’ve entered, and it also alerts them to any further activity that people connected to that email address or that IP address do in the future. XKeyscore consists of over 700 servers at approximately 150 sites where the NSA collects data.
Another component of NSA data collection is a program called Marina that is a database and analysis toolset for intercepted internet metadata. The database stores metadata up to a year. The Marina metadata application tracks a user’s browser experience, gathers contact information/content and develops summaries of the target and of the more distinguishing features and can look back on the last 365 days’ worth of metadata seen by collection system, regardless whether or not it was tasked for collection. The stored metadata is mainly used for pattern-of-life analysis.
US PERSONS ARE NOT EXEMPT BECAUSE METADATA IS NOT CONSIDERED DATA BY US LAW (SECTION 702 OF THE FISA AMENDMENTS ACT).
 Once the data is collected and can be queried and targeted, the data is then stored in an NSA program called Sentient World Simulation. This program is developing billions of individual nodes (prisons) to reflect every man, woman, and child.
Once the data is collected and can be queried and targeted, the data is then stored in an NSA program called Sentient World Simulation. This program is developing billions of individual nodes (prisons) to reflect every man, woman, and child.
It will be a synthetic mirror of the real world with automated continuous calibration with respect to current real-world information. SWS provides an environment for testing Psychological Operations (PSYOPs), so that military leaders can develop and test multiple courses of action to anticipate and shape behaviors of adversaries, neutrals, and partners (US citizens).
SWS also replicates financial institutions, utilities, media outlets, and street corner shops. By applying theories of economics and human psychology, its developers can predict how individuals and mobs will respond to various stressors.
These three programs, XKeyscore, Marina, and Sentient World Simulation create some of the environments which intend to imprison and control those who willingly enter the digital virtual reality of the internet. The internet is a WARZONE according to the people who created and weaponized it. Notice that the description of SWS says that even “neutrals” are the target of these systems. No one is safe from the surveillance, monitoring, targeting, and attacks of Facebook, Twitter, Google and Alphabet.
Just look how President Donald Trump is using Twitter as a weapon against the Main Stream Media. There is a battle for information and every person is in the middle of the battle whether they like it or not. The only question is whether you will be manipulated or not, which unless you are a hermit, you will be manipulated. So the real questions is – to what extent?
The largest domestic military exercises in US history happened in 2015. They were entitled: “Jade Helm 2015 – Mastering the Human Domain.” This title of the exercises should indicate to you where the US military is focusing its time and energy these days – on US citizens. It also clearly tells us what the intent of the US military is – to Master the Human Domain.
DARPA’S DARK HISTORY
In 2001, under the Total Information Awareness Program, President Bush had secretly authorized the NSA’s domestic surveillance of Americans without court-approved warrants. This was also the year that the Bush administration drew up its Information Operations Roadmap. Describing the internet as a “vulnerable weapons system,” Donald Rumsfeld’s Information Operations roadmap advocated that Pentagon strategy “should be based on the premise that the Department of Defense will ‘fight the net’ as it would an enemy weapons system.” The US should seek “maximum control” of the “full spectrum of globally emerging communications systems, sensors, and weapons systems,” advocated the document.
As of 2006, the CIA’s SAIC (Science Applications International Corporation) had been awarded a multi-million dollar NSA contract to develop a big data-mining project called ExecuteLocus, despite the colossal $1 billion failure of its preceding contract, known as Trailblazer. Core components of Total Information Awareness were being quietly continued under new code names. The new surveillance program was then fully transitioned from DARPA’s jurisdiction to the NSA.
Thus, 100% illegal surveillance was, and now is, possible.
Every project of DARPA and In-Q-Tel have been weaponized before they are shared with the companies who then are the “front” for a DARPA sponsored company. DARPA and In-Q-Tel keep the encryption codes and build in backdoors so that they can always control the military weapons that have been released into the corporate world for public use. According to DARPA and In-Q-Tel, innovation and technological advances must first be a weapon that can be controlled by its makers – the military.

The Highlands Forum (controls DARPA-In-Q-Tel) directed the creation of weapons of every sort that have been released into the corporate world and now control your laptop, phone, computer, and every other device with a “bugged” microprocessor inside. Intel microprocessors are found in most of our “private” digital devices and are, in fact, collecting “intelligence” for the Department of Defense, CIA, and NSA.
DARPA/In-Q-Tel and the Highlands Forum drive the process of continuous war, from creating the devices that control all nuclear weapons to incubating the technologies that created the Internet, Intel micro-processers, Cisco routers, Google search engines, Facebook-like social networks, the Internet of Things, cell phones, Microsoft software, MacAfee security software, and all other commercial and military warfare devices using their source code.
US PATENT OFFICE WORKS FOR DARPA/IN-Q-TEL
Over five thousand patents have been legal confiscated (stolen) by the US patent office and give to DARPA/In-Q-Tel for further development and weaponization. Once the patent is used to create a prototype, it has encrypted back-doors installed then it is given out as open source material for corporations and individuals to bring to the market place. If an inventor of a patent that is confiscated by the US Patent Office tries to continue work on the patent, that inventor may end up in jail. There are US patent laws permitting the government to steal and suppress any new technology (and imprison the inventor) which threatens “national security.”
For more detail on the corruption of the US Patent Office, please see our blockbuster report here:
FACEBOOK UNMASKED: HOW THE WORLD’S MOST RELEVANT ENTREPRENEUR WAS SCREWED BY ZUCKERBERG
CISCO SYSTEMS MONOPOLY
Once DARPA had created the ARPANET and it proved to be extremely effective, routers were created that could handle exchanges between systems and computers. In 1998, virtually every internet exchange went through a Cisco router. In 2010, a researcher at IBM publicly revealed a flaw in a Cisco operating system that allows a hacker to use a backdoor that was supposed to be available only to law enforcement agencies.
The intruder could hi-jack the Cisco device and use it to spy on all communications passing through it, including the content of e-mails, leaving products vulnerable to attack, particularly ubiquitous software programs like those produced by Microsoft. This backdoor puts millions of customers and their private information at risk and jeopardizes the security of electrical power facilities, public utilities, and transportation systems.
 INTEL (IN-Q-TEL) INSIDE
INTEL (IN-Q-TEL) INSIDE
Inside every Intel microprocessor is a smaller processor that lets Intel – who works for the Department of Defense – control every aspect of your computer remotely no matter what encryption codes you use. All Intel microprocessor chips have a built-in backdoor that allows complete remote access to a PC through a second physical processor embedded within the main processor which has its own operating system embedded on the chip.
It is advertised as something that will allow IT professionals to remotely troubleshoot a PC. Intel’s latest x86 chips contain a secret backdoor with an embedded subsystem called the Management Engine (ME) that functions as a separate CPU and cannot be disabled, and the code is proprietary. Even an encrypted hard drive can be monitored and controlled by the “processor within the processor” that already has your encryption key. There is more than just the NSA monitoring your calls, emails, and transmissions — there is Intel “Inside” your computer.
Intel collects “intelligence” but it also provides a “back door” to control, or “turn off” your computer at will, just like it has been demonstrated that Cisco routers have a “back door” open to the NSA. A backdoor is a method of bypassing normal authentication in a cryptosystem used for securing unauthorized remote access to a computer.
See our detailed citizens intelligence report on Intel here:
DARPA VADER AND THE EVIL INTEL EMPIRE INSIDE UNCOVERING THE DOD SITH LORDS THAT CONTROL YOUR LAPTOP
IN-Q-TEL IS WARFARE TECHNOLOGY
In 1999, the CIA created its own venture capital investment firm, In-Q-Tel, to fund promising start-ups that might create technologies useful for intelligence agencies just as the Department of Defense had years earlier created DARPA. Both groups are controlled by the Highlands Forum (Group). The Highlands Forum provides the ideas and funding for the scientific weaponization of new inventions through cooperation between the military and corporate contractors. Its biggest successes recently have been led by the CIA’s In-Q-Tel in the development of high-tech network-based cyber-warfare.
In-Q-Tel contracts almost all its work through SAIC (Science Applications International Corporation) that changed its name to Leidos in 2013. Leidos is among the top 10 largest defense contractors in the U. S. and has a symbiotic relationship with the NSA and U. S. intelligence agencies.
The Highland Forum, DARPA, and In-Q-Tel are a secret multi-national high-tech think tanks for inventing and the control of innovations that can be turned into weapons. Military and information technology experts gather at the Highlands Forum meetings to consider the impacts of the globalization of IT on U. S. interests and warfare. The Forum developed the idea of “network-centric warfare” which is now a top concern of the military and the corporations that serve it.
DARPA’S GOOGLE
The US intelligence community funded, nurtured and incubated Google as a military weapon to control information. Seed-funded by the NSA (DARPA) and CIA (In-Q-Tel & SAIC), Google was one among a group of private sector start-ups co-opted by US intelligence to control information warfare.
In 1994, two PhD students at Stanford University, Sergey Brin and Larry Page, made their breakthrough on the first automated web crawling and page ranking application built upon the source code given to them by DARPA/In-Q-Tel. That application remains the core component of what eventually became Google’s search service. Brin and Page had performed their work with funding from the Digital Library Initiative (DLI), a multi-agency program of the National Science Foundation (NSF), NASA and DARPA.
The NSA needed to control and monitor digital information, particularly the data flowing over the Internet. The government can “command” that any company must turn over that information, and it does so as part of the NSA’s Prism program, which Google had been participating in for years by the time it signed the cooperative agreement with the NSA.
Under Google’s terms of service, the company advises its users that it may share their “personal information” with outside organizations, including government agencies. Essentially, the United States intelligence community funded, nurtured and incubated Google as part of a drive to dominate the world through control of information.
NO ONE CHECKS WHETHER DARPA INVENTIONS ARE MORAL, ETHICAL, OR HUMANE. ALL MILITARY INVENTIONS, EVEN IF THEY ADVERTISE THEM AS HELPFUL, ARE WEAPONIZED.
Let’s take a closer look at the Highland Forums. The description below is taken from their website:
Highland Forums Program Description Overview
“Information Warfare, Information Operations, Information Assurance, and Operational Resilience Information is an instrument of national, global, and corporate power. As such, control over its use, its protection, and its manipulation, are national and global security issues. This Research Program examines strategic and tactical offensive and defensive aspects of information operations (IO) by state and non-state actors to achieve political, military, and economic goals through IO means, including computer network operations (CNO), computer network attack (CNA), computer network exploitation (CNE), computer network defense (CND), psychological operations (PSYOPS), perception management, media manipulation, propaganda, strategic influence, and public diplomacy, among others.”
THE CIA’S – IN-Q-TEL, SAIC, AND LEIDOS
In 1998, the CIA identified technology as a top strategic priority, and set out a bold and radical plan to create a new venture that would help increase the agency’s access to private sector innovation. In-Q-Tel was chartered in February 1999 by a group of private citizens at the request of the Director of the CIA and with the support of the U.S. Congress. In-Q-Tel was tasked with building a bridge between the intelligence community and a new set of technology innovators. Eventually, In-Q-Tel evolved into the Science Applications International Corporation (SAIC).
Leidos, a joint spin-off of Science Applications International Corporation (SAIC), is an American defense company headquartered in Reston, Virginia, that provides scientific, engineering, systems integration, and technical services. Leidos works extensively with the Department of Defense (4th largest DoD contractor FY2012), the Department of Homeland Security, and the United States Intelligence Community, including the NSA, as well as other US government civil agencies and selected commercial markets. On September 27, 2013, SAIC changed its name to Leidos and spun off a $4 billion government services and information technology company, which retains the name Science Applications International Corporation.
SAIC PROJECTS
In March 2001, SAIC defined the concept for the NSA Trailblazer Project. Trailblazer was a continuation of the earlier ThinThread program which was a project that the NSA pursued during the 1990s. The program involved wiretapping and sophisticated analysis of the resulting data. ThinThread was dismissed and replaced by the Trailblazer Project, which lacked privacy protections. A consortium led by SAIC was awarded a $280 million contract to develop Trailblazer in 2002.
Trailblazer was intended to develop a capability to analyze data carried on all communications networks. It was specifically intended to track entities using cell phones and e-mail. In 2002, NSA contracted SAIC for $280 million to produce a “technology demonstration platform” for the agency’s project, a “Digital Network Intelligence” system to analyze data carried on computer networks.
CYBERSPACE – A NEW OPERATIONAL DOMAIN
In 2011, the United States Department of Defense named cyberspace a new operational domain. The cyberspace domain provides critical capabilities that enable the military to conduct operations in all domains (Land, Sea, Air, Space, and Cyberspace). The US Cyber Command and the Military Services are working to integrate the cyberspace domain with the other operational domains in order to conduct military command and control and achieve “national security” objectives. To effectively integrate cyberspace operations, DoD requires situational awareness of the Mission, Network, and Adversary based on analysis of operational data to make timely and effective decisions.
IT IS OFFICIAL, EVERY TIME YOU ARE ON THE INTERNET, YOU ARE IN A CYBER WAR-ZONE AS DEFINING BY THE US DEPARTMENT OF DEFENSE. YOU ARE CONSIDERED A “HOSTILE ACTOR” UNTIL NEUTRALIZED.
NSA CYBER-KINETIC ATTACKS
The military has for years been developing offensive capabilities, giving it the power not just to defend the US but to assail its foes. Using so-called cyber-kinetic attacks, the NSA and its forces now have the capability to physically destroy an adversary’s equipment and infrastructure, and potentially even to kill. The NSA has concluded that such cyber weapons are as crucial to 21st-century warfare as nuclear arms were in the 20th.
 Cyber warriors have already launched their first attack. The cyber-weapon that came to be known as Stuxnet was created and built by the NSA in partnership with the CIA and Israeli intelligence in the mid-2000s. The first known piece of malware designed to destroy physical equipment, Stuxnetwas aimed at Iran’s nuclear facility in Natanz. By surreptitiously taking control of an industrial control link known as a Scada (Supervisory Control and Data Acquisition) system, the sophisticated worm damaged about a thousand centrifuges used to enrich nuclear material.
Cyber warriors have already launched their first attack. The cyber-weapon that came to be known as Stuxnet was created and built by the NSA in partnership with the CIA and Israeli intelligence in the mid-2000s. The first known piece of malware designed to destroy physical equipment, Stuxnetwas aimed at Iran’s nuclear facility in Natanz. By surreptitiously taking control of an industrial control link known as a Scada (Supervisory Control and Data Acquisition) system, the sophisticated worm damaged about a thousand centrifuges used to enrich nuclear material.
But Stuxnet is only the beginning. The NSA has recruited thousands of computer experts, hackers, and engineering PhDs to expand US offensive capabilities in the digital realm. The Pentagon has requested $4.7 billion for “cyberspace operations,” even as the budget of the CIA and other intelligence agencies could fall by $4.4 billion. It is pouring millions into cyber defense contractors. And more attacks may be planned.
On a remote stretch of desert in central Utah, the NSA has built a massive, 1 million-square-foot data warehouse. Costing more than $1.5 billion, the highly secret facility is designed to house upward of trillions of intercepted phone calls, e-mail messages, Internet searches and other communications intercepted by the agency as part of its expansive eavesdropping operations. The NSA is also completing work on another data warehouse, this one in San Antonio, Texas.
Microsoft shares zero day vulnerabilities in its products with the NSA before releasing a public alert or a software patch. McAfee, the internet security company owned by Intel, provides the NSA, the CIA, and the FBI with network traffic flows, analysis of malware, and information about hacking trends.
Companies that promise to disclose holes in their products only to the spy agencies are paid for their silence. To an extent, these openings for government surveillance are required by law. Telecommunications companies, in particular, must build their equipment in such a way that it can be tapped by a law enforcement agency presenting a court order.
DESCRIPTION OF PSYOPS FROM A MILITARY DOCUMENT
The document: Intelligence and Electronic Warfare Support to Psychological Operations is based upon Special Operations Forces Intelligence and Electronic Warfare Operations, Field Manual No. 34-36 published on 30 September, 1991, by Department of the Army Headquarters in Washington DC.
Missions
PSYOP missions are planned products and psychological actions in peace or war that are directed toward foreign enemy, friendly, and neutral audiences. The purpose is to influence attitudes and behaviors to achieve national political and military objectives.
PSYOP supports varied military, political, and diplomatic actions across the operational continuum. These missions can be strategic, operational, or tactical missions.
Strategic PSYOP missions are conducted at the national or theater level to advance broad, long-term psychological objectives in support of national psychological objectives.
WHAT NEW EVIL IS THE HIGHLANDS FORUM UP TO NOW
By 2008, the NSA was effectively resurrecting the Total Information Awareness project with a focus on internet data-mining via comprehensive monitoring of e-mails, text messages, and Web browsing. We also now know that the NSA’s XKeyscore ‘Digital Network Intelligence’ exploitation system was designed to allow analysts to search not just internet databases like emails, online chats and browsing history, but also telephone services, mobile phone audio, financial transactions and global air transport communications — essentially the entire global telecommunications grid.
In 2009, it also emerged from a Google patent application that the company had deliberately been collecting ‘payload’ data from private wi-fi networks that would enable the identification of “geolocations.” In the same year, Google had signed an agreement with the NSA giving the agency open-ended access to the personal information of its users, and its hardware and software, in the name of cyber security.
It is not just Google that is a key contributor and foundation of the US military-industrial complex – it is the entire internet, and the wide range of private sector companies — many nurtured and funded under the mantle of the US intelligence community which sustain the internet and the telecoms infrastructure. It is also the myriad of start-ups selling cutting edge technologies to the CIA’s venture firm In-Q-Tel, where they can then be adapted and advanced for applications across the military intelligence community.
In 2011, the Forum hosted two DARPA-funded scientists, Antonio and Hanna Damasio, who are principal investigators in the ‘Neurobiology of Narrative Framing’ project at the University of Southern California. Evoking Zalman’s emphasis on the need for Pentagon psychological operations to deploy “empathetic influence”, the new DARPA-backed project aims to investigate how narratives often appeal “to strong, sacred values in order to evoke an emotional response,” but in different ways across different cultures.
THE MOST DISTURBING ELEMENT OF THE RESEARCH IS ITS FOCUS ON TRYING TO UNDERSTAND HOW TO INCREASE THE PENTAGON’S CAPACITY TO DEPLOY NARRATIVES THAT INFLUENCE LISTENERS IN A WAY THAT OVERRIDES CONVENTIONAL REASONING IN THE CONTEXT OF MORALLY-QUESTIONABLE ACTIONS.
DARPA’s goal is to mine millions of American weblogs as part of its ‘neurobiology of narrative framing’ research. As the Pentagon’s extensive funding of propaganda on Iraq and Afghanistan demonstrates, population influence and propaganda is critical not just in far-flung theatres abroad in strategic regions, but also at home, to quell the risk of domestic public opinion undermining the legitimacy of Pentagon policy.
CONTROLLING AMERICANS THROUGH THE INTERNET
It is important to remember that since Barack Obama added new language in the National Defense Authorization Act of 2012, Americans are now seen as possible terrorists and thus are military targets and enemies of the state, unless proven otherwise. In essence, all of the above cyberwarfare programs are being used on Americans indiscriminately and with ill intent.
The Patriot Act, later called the US Freedom Act is the exact opposite of its name – it takes away freedom from patriots and lets multi-national corporations and the “run-away military” use the American people as cyberwarfare testing grounds.
THIS FACT IS LITTLE KNOWN, THAT THE US MILITARY IS NOW ALLOWED TO ACT WITHIN THE BORDERS OF AMERICA AND TARGET AMERICANS AS HOSTILE WAR-ACTORS (AS THE MILITARY CALLS US).
We are in an information war and the stakes are high – American freedom or military/corporate control. This battle wages while many people are complacent and perfectly happy with their addiction to their cellphone, the internet, and social media. Many mindless followers can’t wait until every electronic devise they own is connected to the Internet of Things.
The Internet is a weapon and it is our job to find out what the battle is all about and make sure that we retain our US Civil Rights and American freedom and liberty.
We must call out DARPA and In-Q-Tel for their patent thefts, continuous lies, and cyberwarfare manipulations and demand that taxpayer dollars that funded these evil weaponized tools be acknowledge and that those cyber-tools be turned over to Americans without the spy systems and information control systems attached.
We need a free and private internet and social networks that are not manipulated as a tool that intends to control our very thinking.
Remember that the intent is to “master the human domain” via the mechanical domain controlled by warlords who wish to take our freedoms away.
We the People demand that these companies (and any others like them) that were financially seeded and funded by US taxpayers, BE GIVEN TO THE PEOPLE AS A PUBLIC UTILITY and that the fictitious owners of these companies be prosecuted for patent infringement.
APPENDIX
DARPA Programs
Below is a short list of DARPA/In-Q-Tel projects that have been declassified. This is just the tip of the iceberg. Just imagine, if they are willing to declassify programs about mind-control and psyops, what are the programs and projects that they are not willing to share with us. This list is daunting, frightful, and disturbing. It is not for the weak of heart but so many patriots have asked us to make the lists available again that we had to shine the flood lights on this criminal cartel.
Social Media in Strategic Communication (SMISC) program is an attempt to get better at both detecting and conducting propaganda campaigns on social media. SMISC has two goals. First, the program needs to help the military better understand what’s going on in social media in real time – particularly in areas where troops are deployed. Second, Darpa wants SMISC to help the military play the social media propaganda game itself.
The Pentagon is building a tool to identify social media propaganda campaigns that produces counter-spin through computer artificial intelligence.
Interactive Facial Recognition in Real Time – BBC facial recognition programs help predict the success or failure of television programming. In the past, the BBC has used its facial recognition technology, built by in-house startup CrowdEmotion, to track 4,500 faces as people watched show trailers to see what kinds of emotions the commercials produced. They’ve also looked at how hundreds of study participants react to programs like Top Gear and Sherlock. http://fortune.com/2016/02/13/bbc-ads-crowdemotion/
The company CrowdSight uses facial recognition software in real time. They advertise on their website: “Understand and Predict your Audience! Deliver Better Experiences by Knowing their Emotional Behavior and Engagement in Real-time. CrowdSight Software Development Kit (SDK) is a flexible and easy-to-integrate Crowd Face Analysis Software which allows you to gather real-time, anonymous information about your audience while they behave spontaneously in different life environments. Understand your audience emotional reactions and engagement towards your products, content and campaigns, and recognize important demographics such as age, gender and ethnicity, in real-time. CrowdSight works offline and on the most popular desktop and mobile platforms (Windows, Mac, Linux, iOS, Android).”
http://sightcorp.com/crowdsight/
Visual Evoked Potential (VEP) – A VEP is an electrical potential recorded after a subject is presented with a type of visual stimuli. There are several types of VEPs. Steady-state visually evoked potentials (SSVEPs) use potentials generated by exciting the retina, using visual stimuli modulated at certain frequencies. SSVEP’s stimuli are often formed from alternating checkerboard patterns and at times simply use flashing images. SSVEP has proved to be successful within many BCI systems. This is due to several factors, the signal elicited is measurable in as large a population as the transient VEP and blink movement and electro-cardiographic artefacts do not affect the frequencies monitored.
Synthetic Telepathy and Silent Communication – In a $6.3 million Army initiative to invent devices for telepathic communication, Gerwin Schalk, underwritten in a $2.2 million grant, found that it is possible to use ECoG signals to discriminate the vowels and consonants embedded in spoken and in imagined words. The results shed light on the distinct mechanisms associated with production of vowels and consonants, and could provide the basis for brain-based communication using imagined speech. Research into synthetic telepathy using sub-vocalization is taking place at the University of California, Irvine under lead scientist Mike D’Zmura. The first such communication took place in the 1960s using EEG to create Morse code using brain alpha waves.
Using EEG to communicate imagined speech is less accurate than the invasive method of placing an electrode between the skull and the brain. On February 27, 2013 the group of Miguel Nicolelis at Duke University and IINN-ELS successfully connected the brains of two rats with electronic interfaces that allowed them to directly share information, in the first-ever direct brain-to-brain interface. On 3 September 2014, scientists reported that direct communication between human brains was possible over extended distances through Internet transmission of EEG signals.
Sentient World Simulation – The DoD is developing a parallel to Planet Earth, with billions of individual “nodes” to reflect every man, woman, and child this side of the dividing line between reality and AR. Called the Sentient World Simulation (SWS), it will be a “synthetic mirror of the real world with automated continuous calibration with respect to current real-world information”, according to a concept paper for the project.
“SWS provides an environment for testing Psychological Operations (PSYOP),” the paper reads, so that military leaders can “develop and test multiple courses of action to anticipate and shape behaviors of adversaries, neutrals, and partners.” SWS also replicates financial institutions, utilities, media outlets, and street corner shops. By applying theories of economics and human psychology, its developers believe they can predict how individuals and mobs will respond to various stressors.
http://www.theregister.co.uk/2007/06/23/sentient_worlds/
Insight Program – DARPA awarded a $14 million contract to SAIC for the DARPA Insight program, which is intended to help U.S. intelligence experts detect threat networks, irregular warfare, and terrorist operations by combining intelligence information from imaging sensors, crowd-source and other social network or text-based sensors, as well as from other sources for further analysis. The program seeks to fill gaps in current U.S. intelligence, surveillance and reconnaissance (ISR) systems that center on the inability to exploit and cross-cue several different intelligence sources automatically.
The DARPA Insight program seeks to develop integrated human/machine reasoning into intelligence equipment to encompass operator knowledge and reasoning when dealing quickly with complex data from many different sensors. SAIC experts will concentrate on these areas in building the Insight next-generation ISR analysis system.
SAIC experts will build model-based behavioral correlation, modeling, prediction, and threat network analysis tools that combine intelligence information across many different sources automatically to improve the efficiencies of multi-intelligence sensors. The company also will develop a unified data-management and processing environment that integrates new intelligence sensors and software algorithms.
EM fields and Hidden symbols – DARPA is revealing programs, which have existed for years, to develop methods and techniques to incept thoughts and ideas into the mind. They reveal how once a mind has been programed with the memory patterns, words and symbols can trigger the programing without the need of the original device.
Mind Control Project – The aim of this program is to remotely disrupt political dissent and extremism by employing “Transcranial Magnetic Stimulation” (TMS) in tandem with sophisticated propaganda based on this technology. TMS stimulates the temporal lobe of the brain with electromagnetic fields. The program, conducted by The Center for Strategic Communication, is based at Arizona State University.
This research aims to literally induce or disrupt the operation of narratives within the brain. In other words, this research aims to stop individuals from thinking certain thoughts and make others believe things they normally would not believe. This research has tremendous interrogation possibilities and could potentially be used to more successfully spread propaganda or stop political upheaval to an unsuspecting public. This research is being conducted by The Center for Strategic Communication at ASU and is entitled “Toward Narrative Disruptors and Inductors: Mapping the Narrative Comprehension Network and its Persuasive Effects”.
Transcranial Magnetic Stimulation is a very powerful tool used to impair the brain functioning of individuals. See the videos below for a brief demonstration of the effects of TMS. http://youtu.be/XJtNPqCj-iA or http://youtu.be/FMR_T0mM7Pc
Once the research group determines which parts of the brain are associated with cognitive reasoning and narrative comprehension, they attempt to impair those sections in order to “create a fundamental basis for understanding how to disrupt or enhance aspects of narrative structure and/or brain functioning to minimize or maximize persuasive effects on subject proclivity to engage in political violence.
Once it is determined that disruption of certain portions of the brain can enhance persuasive messaging, individuals can be persuaded to do things they normally would not do and believe things they normally would not believe.
It offers the capability to induce or disrupt the operation of narratives in the brain, and develops the capability to induce narrative validity.
Mechanical disruptions of narrative processing may be, ultimately, replicated through targeted strategic communication campaigns that approximate the narrative disruptions induced via magnetic stimulation.
Through extensive research, they may be able to replicate the machine’s brain disrupting functioning simply through carefully crafted and researched persuasive messages and propaganda. With enough data, the government could spread propaganda through the media that people will almost automatically believe, whether it is true or not.
In terms of interrogation possibilities, Transcranial Magnetic Stimulation can be forced upon individuals to make them believe certain things, say certain things, and perhaps admit to acts they did not actually commit (as the TMS can induce narrative validity), or commit acts they normally would not commit.
The Brain Project – This area of study has received $100 million in funding via Obama’s ten-year BRAIN Project, as well as a $1.3 billion commitment from Europe. Concurrently, there is heavy military funding through agencies such as the Defense Advanced Research Projects Agency (DARPA). This raises the question of transparency when a “black budget” often justifies total secrecy in the name of national security.
Neuroscientists Successfully Plant False Memories – MIT neuroscientists have shown that they can plant false memories. They also found that many of the neurological traces of these memories are identical in nature to those of authentic memories. Most of the research in this area currently revolves around how to induce and eliminate fear. The study also provides further evidence that memories are stored in networks of neurons that form memory traces for each experience we have. Scientists already know how to set off an emotional response in combat veterans by simulating a specific set of frequencies that have become associated with wartime experience.
http://sitsshow.blogspot.com/2013/08/disclosure-darpa-reveals-mass-mind.html
http://www.militaryaerospace.com/articles/2011/05/darpa-chooses-saic.html
Total Information Awareness – Under the umbrella of a system known as Total Information Awareness, DARPA spearheaded many of the surveillance programs abused by the NSA. DARPA’s Total Information Awareness concept created a veritable buffet of advanced surveillance and data mining programs, many of which ultimately were folded into NSA’s PRISM. We now know that PRISM culled citizens’ personal data from companies like Microsoft, Google, and Facebook, and was later leaked by whistleblower Edward Snowden.
Evidence Extraction and Link Discovery program (EELD) – Sole purpose is to gather as much information about both terror suspects and average American citizens as possible, using phone records, computer searches, credit card receipts, parking receipts, books checked out of the library, films rented, and more. Goal is to assess megadata on 285 million people a day in real-time.
Scalable Social Network Analysis (SSNA) – Program monitors telephone calls, conference calls, and ATM withdrawals … also sought to develop a far more invasive surveillance technology.
Activity Recognition and Monitoring (ARM) – With England’s CCTV surveillance cameras as a model, ARM created a massive database of people going about their everyday lives. Using advanced facial recognition software, the program highlighted any behavior that was outside the realm of a preprogrammed “ordinary,” the definition of which remains classified.
Deep Exploration and Filtering of Text (DEFT) – Operating on a $28 million dollar budget, this program utilizes advanced computer algorithms to analyze text-based messages in all shapes and forms, from text messages to reports, with the aim being to comprehend “implied and hidden meanings through probabilistic inference.”
Nexus 7 – With a classified budget, this particularly program studies and tracks social network content. First used in Afghanistan in a defense capacity, when aimed at domestic networks the use of the program is a mystery.
Narrative Networks Program – Developed classified techniques used to manipulate trust in humans. For its Narrative Networks (N2) program, DARPA collaborated with a CIA agency called the Intelligence Advanced Research Projects Agency (IARPA) to develop methods of overwriting messages in the human mind. The program was described as having two parts: first, to understand what happens in the human mind when someone sees or hears a message; second, to figure out how to control how the brain interprets the message.
In-Q-Tel Projects
Recorded Future – Using what they call a “Temporal Analytics Engine,” Recorded Future (RF) provides forecasting and analysis tools to help analysts predict future events by scanning sources on the Internet, and extracting, measuring, and visualizing the information to show networks and patterns in the past, present, and future. As of 2015 the engine was described as “Web Intelligence Engine Visible Technologies – social media monitoring.
Digital Reasoning – Since 2012, the firm has sold its Synthesys software to banks and hedge funds, including UBS and Point72 Asset Management. Financial institutions use Synthesys to scan internal e-mails within a given company in search of unfamiliar patterns between employees, in terms of word-specific content, frequency and interpersonal connections. The aim is to predict fraud before it occurs.
Palantir – Palantir Technologies, Inc. is a private American software and services company, specializing in data analysis. The company is known for two software projects in particular: Palantir Gotham is used by counter-terrorism analysts at offices in the United States Intelligence Community and United States Department of Defense, fraud investigators at the Recovery Accountability and Transparency Board, and cyber analysts at Information Warfare Monitor.
CallMiner – Phone speech analytics software
MASINT – Remote tracking, surveillance, and extraction of brain-waves typifying thought-forms, emotional states, analytic mind states, and others
Mohomine mohoClassifier – Organizes mass data
3VR – 3VR Inc. develops software enabling organizations to mine data from video. 3VR works with leading banks, governments, law enforcement and retailers at the moment.
Adaptx – Creates digital pens that speed up field data collection.
Basis Technology – Synthesizes the foreign chatter and provides software for text analytics in over twenty languages. They work primarily in applied natural language processing, deriving meaning from the ways people actually use language.
Cloudera – Large-scale data storage. Cloudera Enterprises is one of the most cost-effective ways for companies to securely carry out large-scale data analysis and storage.
FireEye – FireEye is one of the most advanced cybersecurity firms and specializes in protecting against botnet attacks and also works to combat the malware that brings computers into the network.
The Ember Corporation – Ember Corporation focuses on developing networking systems that simplify wirelessly networking low-power products. They’re focused on smart energy, remote monitoring, and remote control uses of their tech.
Infinite Z – Virtual-holographic simulation a reality through an interactive 3D environment.
OpenSpan – Makes software that enables organizations to see exactly what employees are doing on their computer: what programs they’re using, what progress they’re making, etc.
Seventh Sense – Develops health monitoring products that interface with human skin
Sonitus Medical – Makes a hearing system that transmits sound imperceptibly through the mouth. The SoundBite hearing system plays off the principle of bone conduction to transmit audial messages. A nearly invisible in-the-mouth hearing and communication platform is non-invasive and connects directly to the inner ear, allowing the user to hear transmitted messages through their skull.
Spotter RF – Makes super-powerful radars in a handheld form that can track a person walking anywhere within a 148 acre space, and it’s handheld.
Visible Technologies – Extracts business solutions from social media chatter with software that allows users to extract business value from social communities, and also give customer insights for brands online.
Walleye – Makes handheld devices that can see into and through solid objects
In-Q-Tel and DARPA Mind Control Programs
Real-time Contextual Overlays for Live Streams – A system and method for contextualizing and live-updating overlay data for live media streams. Overlays can be generated in real-time and in response to live events. US 20130311595 A1 November 21, 2013. Google Inc.
Method and Apparatus for Remotely Determining Emotional States – A waveform energy having a predetermined frequency and intensity is generated and wirelessly transmitted towards a subject. Physiological or physical parameters of blood pressure, pulse rate, pupil size, respiration rate and perspiration level are measured for evaluating criminal intent in security sensitive areas. US 5507291 A – April 5, 1994
Sounds of Silence – The Silent Subliminal Presentation System (SSPS) – Silent Subliminal Presentation System was developed for commercial use in 1992. A silent communications system in which nonaural carriers, in the very low (ELF) or very high audio-frequency (VHF) range or in the adjacent ultrasonic frequency spectrum are amplitude – or frequency- modulated with the desired intelligence and propagated acoustically or vibrationally, for inducement in to the brain, typically through the use of loudspeakers, earphones, or piezoelectric transducers. The modulated carriers may be transmitted directly in real time or may be recorded and stored on mechanical, magnetic, or optical media for delayed or repeated transmission to the listener. US Patent#5,159,703
Flame – The program is able to turn on a target’s Web cam and record video remotely and without detection.
Multidisciplinary Research Program of the University Research Initiative (MURI), Recognize/predict social contexts, relationships, networks, and intentions from social media, taking into account non-verbal communication such as gestures, micro-expressions, posture, and latent semantics of text and speech. Create algorithms for prediction and collection of latent signals and their use in predicting social information.
Beware – Analyses people’s social media activity, property records, the records of friends, family or associates, among other data, to assign suspects a so-called “threat-score.” That “threat-score” can then be used by police to pre-judge if a suspect is going to be dangerous, and to adapt their approach accordingly.
Iraqi Silent Sound Program – US Psy-Ops teams set up FM transmitters, utilizing Iraqi frequencies and overpowered the local station. Along with patriotic and religious music, PsyOps transmitted “vague, confusing and contradictory military orders and information.” A sophisticated electronic system designed to ‘speak’ directly to the mind of the listener; to alter and entrain his brainwaves, to manipulate his brain’s electroencephalographic (EEG) patterns and thus artificially implant negative emotional states – feelings of intense fear, anxiety, despair and hopelessness were created in the Iraqi troops. This effective subliminal system implants emotions in the minds of the targeted subject.
Nervous system manipulation by electromagnetic fields from monitors – US Patent and Trade Office, Patent #6,506,148 on subliminal behavior modification, 1/14/2003, United States Patent 6,506,148, Loos, January 14, 2003. Abstract: It is possible to manipulate the nervous system of a subject by pulsing images displayed on a nearby computer monitor or TV set. For the latter, the image pulsing may be imbedded in the program material, or it may be overlaid by modulating a video stream. Physiological effects have been observed in a human subject in response to stimulation of the skin with weak electromagnetic fields that are pulsed with certain frequencies near 1/2 Hz or 2.4 Hz, such as to excite a sensory resonance.
Many computer monitors and TV tubes, when displaying pulsed images, emit pulsed electromagnetic fields of sufficient amplitudes to cause such excitation. It is therefore possible to manipulate the nervous system of a subject by pulsing images displayed on a nearby computer monitor or TV set. For the latter, the image pulsing may be imbedded in the program material, or it may be overlaid by modulating a video stream, either as an RF signal or as a video signal.
The image displayed on a computer monitor may be pulsed effectively by a simple computer program. For certain monitors, pulsed electromagnetic fields capable of exciting sensory resonances in nearby subjects may be generated even as the displayed images are pulsed with subliminal intensity. Inventors: Loos; Hendricus G. (3019 Cresta Way, Laguna Beach, CA 92651), Appl. No.: 872528 Filed: June 1, 2001
Other DARPA/In-Q-Tel Programs
Total Information Awareness – Under the umbrella of a system known as Total Information Awareness, DARPA spearheaded many of the surveillance programs abused by the NSA. DARPA’s Total Information Awareness concept created a veritable buffet of advanced surveillance and data mining programs, many of which ultimately were folded into NSA’s PRISM. PRISM culled citizens’ personal data from companies like Microsoft, Google, and Facebook.
PRISM – A clandestine national security electronic surveillance program operated by the United States National Security Agency which can target customers of participating corporations outside or inside the United States.
Sounds of Silence – The Silent Subliminal Presentation System was developed for commercial use in 1992. A silent communications system in which non-aural carriers, in the very low (ELF) or very high audio-frequency (VHF) range or in the adjacent ultrasonic frequency spectrum are amplitude – or frequency- modulated with the desired intelligence and propagated acoustically or vibrationally, for inducement in to the brain, typically through the use of loudspeakers, earphones, or piezoelectric transducers. The modulated carriers may be transmitted directly in real time or may be recorded and stored on mechanical, magnetic, or optical media for delayed or repeated transmission to the listener. US Patent #5,159,703.
Turbulence – Turbulence is a National Security Agency information-technology project started circa 2005. It was developed in small, inexpensive “test” pieces rather than one grand plan like its failed predecessor, the Trailblazer Project. It also includes offensive cyberwarfare capabilities, like injecting malware into remote computers.
Tailored Access Operations – Intelligence-gathering unit of the NSA that is capable of harvesting approximately two petabytes of data per hour.
Boundless Informant – A system deployed by the NSA to analyze global electronic information. In March 2013, Boundless Informant gathered 14 billion data reports from Iran, 6.3 billion from India, and 2.8 billion from the United States.
Bullrun – A highly classified National Security Agency program to preserve its ability to eavesdrop on encrypted communications by influencing and weakening encryption standards, by obtaining master encryption keys, and by gaining access to data before or after it is encrypted either by agreement, by force of law, or by computer network exploitation (hacking).
Carnivore – A system implemented by the Federal Bureau of Investigation that was designed to monitor email and electronic communications.
DCSNet – The Federal Bureau of Investigation’s point-and-click surveillance system that can perform instant wiretaps on any telecommunications device located in the US.
Fairview – A mass surveillance program directed at foreign mobile phone users.
ICREACH – Surveillance front-end GUI that is shared with 23 government agencies, including the CIA, DEA, and FBI, to search illegally collected personal records.
Magic Lantern – A keystroke logging software deployed by the FBI in the form of an e-mail attachment. When activated, it acts as a trojan horse and allows the FBI to decrypt user communications.
Main Core – A personal and financial database storing information of millions of U. S. citizens believed to be threats to national security. The data mostly comes from the NSA, FBI, CIA, as well as other government sources.
MAINWAY – A NSA database containing metadata for hundreds of billions of telephone calls made through the four largest telephone carriers in the United States.
MUSCULAR – Overseas wiretapping of Google’s and Yahoo’s internal networks by the NSA.
MYSTIC – Is a voice interception program used by the National Security Agency.
Room 641A – A telecommunication interception facility operated by AT&T for the U.S. National Security Agency.
Sentry Eagle – It monitors and attacks an adversary’s cyberspace through capabilities include SIGINT, Computer Network Exploitation, Information Assurance, Computer Network Defense, Network Warfare, and Computer Network Attack. The efforts included weakening U. S. commercial encryption systems.
Special Collection Service – A black budget program that is responsible for “close surveillance, burglary, wiretapping, breaking and entering.” It employs covert listening device technologies to bug foreign embassies, communications centers, computer facilities, fiber-optic networks, and government installations.
Terrorist Finance Tracking Program – A joint initiative run by the CIA and the Department of the Treasury to access the SWIFT (Society for Worldwide Interbank Financial Telecommunication) transaction database as part of the Bush administration’s “Global War on Terrorism.”
Multi-state Anti-Terrorism Information Exchange (MATRIX) – A data mining system originally developed for the Florida Department of Law Enforcement.
Insight Program – It detects threat networks, irregular warfare, and terrorist operations by combining intelligence information from imaging sensors, crowd-source and other social network or text-based sensors, as well as from other sources for further analysis. Develops integrated human/machine reasoning into intelligence equipment to encompass operator knowledge and reasoning when dealing quickly with complex data from many different sensors.
EM Fields and Hidden Symbols – Uses techniques to incept thoughts and ideas into the mind. Once a mind has been programed with the memory patterns, words and symbols can trigger the programing without the need of the original device.
Narrative Networks Program – Developed classified techniques used to manipulate trust in humans. For its Narrative Networks program, DARPA collaborated with a CIA agency called the Intelligence Advanced Research Projects Agency (IARPA) to develop methods of overwriting messages in the human mind.
Mind Control Project – Remotely disrupts political dissent and extremism by employing “Transcranial Magnetic Stimulation” (TMS) in tandem with sophisticated propaganda based on this technology. TMS stimulates the temporal lobe of the brain with electromagnetic fields. This research aims to stop individuals from thinking certain thoughts and make others believe things they normally would not believe. This research is being conducted by The Center for Strategic Communication at ASU and is entitled “Toward Narrative Disruptors and Inductors: Mapping the Narrative Comprehension Network and its Persuasive Effects.” Mechanical disruptions of narrative processing may be, ultimately, replicated through targeted strategic communication campaigns that approximate the narrative disruptions induced via magnetic stimulation. MIT neuroscientists have shown that they can plant false memories. Most of the research in this area currently revolves around how to induce and eliminate fear.
American Intelligence Media Citizens Intelligence Reports that may interest you:
Who Really Owns the Military Industrial Complex explains more about the Highland Forum Group
Weaponization of the Internet and IBM Patent Theft
The Real Energy Revolution Has Begun explains how patent theft has kept amazing technologies from reaching the consumer.
How the World’s Most Relevant Entrepreneur was Screwed by Facebook
Obama-Clinton-Schmidt-Zuckerberg Election Rigging Failed
How Obama Weaponized Cyber Space to Rig Elections
___
http://aim4truth.org/2017/12/19/big-brother-is-watching-you-for-real/

