New Intelligence Briefing Platform Sets the Bar Very High
SOTN Editor’s Note:
The following intelligence briefing comes from the DEEP CONNECTIONS intelligence platform. It focuses on the prevailing gray swans within the global realm of cyberwarfare and cyberterrorism.
Intelligence analyst and gatherer Jim Autio has done an outstanding job pulling together the critical threads that make up the tapestry of today’s ongoing cyber-threats around the world. He quite perceptively points out where and how the Red Queen Hypothesis applies to the lay of the land of cybersecurity across the planet.
What particularly distinguishes this uniquely astute intelligence briefing is that it both synthesizes and integrates several pieces of the cybersecurity puzzle in such a manner so that the user can see not only the outlines of the true picture, but also the crucial reality underlying that picture.
SOTN highly recommends DEEP CONNECTIONS to government and corporate clients alike, especially those requiring a significantly deeper understanding of the rapidly evolving global geopolitical chessboard. The penetrating insights and extremely objective analysis offered at DEEP CONNECTIONS cannot be found anywhere else on the Internet.
For more information and other excellent intelligence briefings on other matters of serious concern, please consult the following link: http://medium.com/deepconnections. Any dedicated geopolitical analyst ought to bookmark this website for Jim’s future intelligence gathering presentations.
State of the Nation
August 27, 2016
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Prevailing Gray Swans: The Clear and Present Danger List for the Week Ending August 19, 2016
4. Cyberterrorism/cyberwarfare/sabotage affecting US infrastructure (e.g. financial markets, power grid, internet)
Deep Background and Threat Forensics: Briefing Focus
[economics | finance | politics | sociology | military strategy|technology]
Introduction: Understanding the Immediacy, Dynamics, Trends, Risks and Scale of the Threat
This intelligence briefing’s objective is to provide concrete evidence that cyberterrorism is a clear and present danger to all modernized societies and is a risk that is growing proportional to the rate of digital technological sophistication and proliferation.
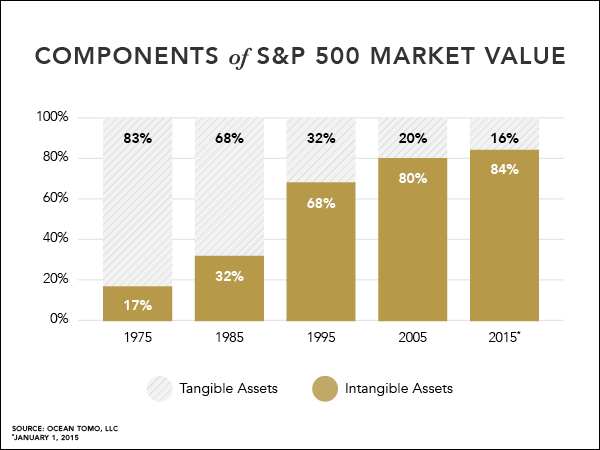
Advances in technology and increases in system complexity spawn and leverage opportunities for future unpredictable vulnerabilities. Considering that 84% of the total value of the S&P 500 now consists of intellectual property (IP) and other intangibles and has been trending higher, during the last decade cybersecurity’s importance should have moved from afterthought to near the apex of awareness and priority. Unfortunately, the protection has woefully lagged for this highly-concentrated societal value that has quietly quintupled since 1975. The cost and risk to not judiciously act is steadily mounting and investment in robust cybersecurity now poses a value equation that mandates planning, resources, talent and urgency. For corporations and infrastructural entities to ignore the exposure and immanent repercussions of cyberterrorism is reckless and bears significant fiduciary responsibility for publicly-held companies and is not limited to economic concerns — public safety and societal well-being is at stake as well.
This document is focused on known threats (cyberterrorism/warfare) and countermeasures to those threats (cybersecurity) at the highest level that impact societal function; it does not address “virus protection” against petty cybercrime for discrete, low-value targets.
To demonstrate the immediacy of some classes of threats see the Norse and Arbor Networks links (these graphs only show overt attacks, many critical security breeches “fly under the radar” and are not discovered for months):
Norse real-time global threat monitoring | Arbor Networks + Google Maps — Digital Attack Map
Finding top-tier, relevant sources for this topic was surprisingly problematic — most is superficial, overdramatized, politically-colored, speculative, or obsolete and, thus, useless for the intent of this briefing. Cyberterrorism and cybersecurity is a rapidly moving battlespace where the most informed experts are in specialized private companies that work in coordination with many aspects of law enforcement and military or are government agencies and specialized military functions. Since detailed government/military sources are classified, many sources for this intelligence briefing were derived from cybersecurity conferences and white papers from the cybersecurity industry* including detailed case studies outlining the process of the extraordinary dynamics and complexity of detecting and combating cyberthreats on infrastructural targets that undergird modern societal function on a global scale.
The Trajectory of Risk: An Accelerating Divergence Between the Perception of Risk and Consequences of the Threat
In business, time is money. In globalized, hyper-competitive environments, getting your product or service to market fast or even too fast (meaning we will fix bugs after the customers discover them) is imperative and is incentivized as such. That being the case, by default, cybersecurity is treated as an accessory and, in effect, becomes a marginalized, outsourced risk: “we’ll do it later.”
From a legal perspective, cyberterrorism, given its economic and existential costs, is a rapidly emerging issue along with its extension — public policy and international law**. Policy lags law while law lags technological advances tied-at-the-hip to its dark flip-side: the advent of new and improved unimaginable harm via weaponized computer code. So this predicament going forward, which is not likely to change because law is a legacy process steeped in inertia, is such that the tandem of technology and harm moves fleetly while law and policy crawls — five years is an eternity and the consequences are grave. Merely ascertaining culpability (legal proof of attribution) is often impossible while assessment of after-the-fact, bottom-line, hard-and-soft costs and incident rate proliferate and stockpile. So the assailant gets away with it but isn’t the corporation liable for negligence given that there is enough precedence to enact and stiffly enforce new laws with radically higher standards imposing serious teeth? The closure of this feedback loop will be a boon to the cybersecurity industry and a wakeup call to corporate boardrooms and a re-defining of their priorities should the threat of data loss, revenue, and goodwill be insufficient to sound the alarm.
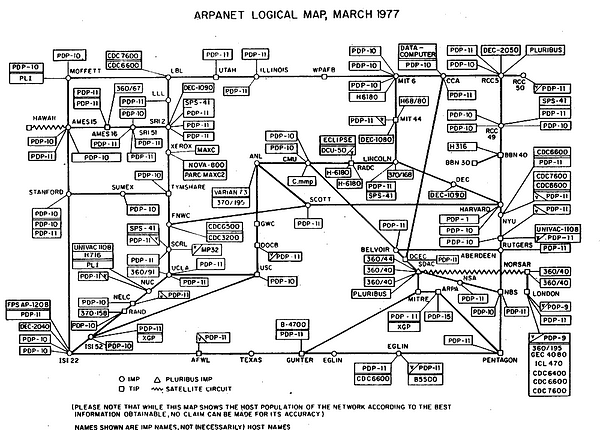
Technically, the internet (i.e. the hardware communications backbone) and the software “world wide web” built on top of it were never envisioned as a global information highway so security was not an integral, high-priority design consideration; in fact, in the 1970s, it was no consideration at all. Malware, trojan horses, worms, viruses, encrypted passwords,cyberwarfare…really?
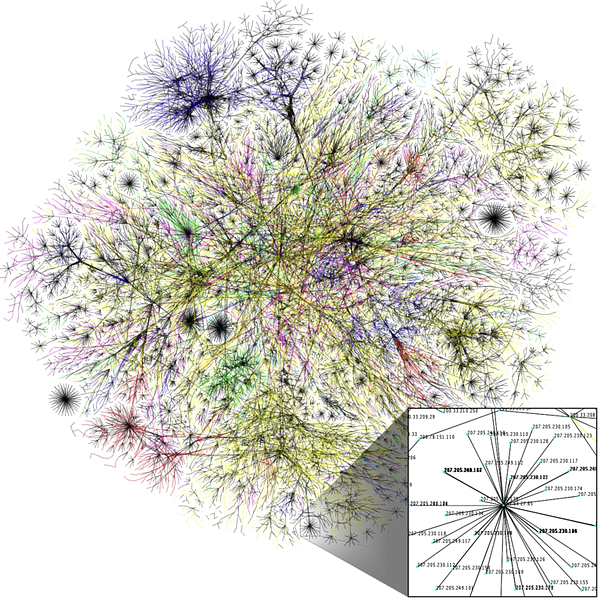
Mission creep from the original design and scope of the internet to what it has become and where it is going (e.g. smart anything coming soon(“Internet of Things”, robots, drones, self-driving cars…) is going to morph into vulnerable everything later) has come to roost as an incubator of a never-ending pipeline of forthcoming, expensive Achilles heels. The cost to society of cyberterrorism to date is only the tip of the iceberg: the dynamic between cyberterrorism and cybersecurity precisely mirrors the classic Red Queen predator-prey ecosystem dynamic in evolutionary biology. The Red Queen hypothesis published in 1973 — coincidently drafted at the same time as ARPANET — has suddenly found new application in the neoteric cyber-ecosystem:
We can think of the Red Queen Hypothesis in terms of an unorthodox game theory. To a good approximation, each species is part of a zero-sum game against other species. Which adversary is most important for a species may vary from time to time, and for some or even most species no one adversary may ever be paramount. Furthermore, no species can ever win, and new adversaries grinningly replace the losers. This is a direction of generalization of game theory which I think has not been explored.
From this overlook we see dynamic equilibria on an immense scale, determining much of the course of evolution by their self-perpetuating fluctuations. This is a novel way of looking at the world, one with which I am not yet comfortable. But I have not yet found evidence against it, and it does make visible new paths and it may even approach reality. [Note: Emphasis mine (J.A.)]
(Source: The University of Chicago, Department of Biology, (Van Valen), Vol. 1, No. 1. p. 21, (1973), “A New Evolutionary Law”) (pdf))

Compounding the Red Queen problem, human perception at the biological level is a formidable, innate barrier to reversing this trend: our perception of loss is grounded in physical threats (is that a saber-tooth tiger behind that tree?) hardwired to our survival whereas threats in cyberspace are both intangible and abstruse, ergo, are very hard to comprehend, value, and effectively act upon — there is a disconnect between our sense of endangerment (i.e. no limbic system-triggered panic or fight-or-flight fireworks) and a proportional response. So, the legal disconnect, the biological disconnect, and the Red Queen problem are structural issues that will never go away which places an incredible burden on the only remedy: the ability to communicate and educate the nature and scale of abstract, clandestine threats that cause real-world devastating aftermaths greater than an ambush of famished saber-tooth tigers. This intelligence bulletin is composed with that tall task in mind.
Understand: the calculus of cost of design and ownership of information systems, cradle-to-grave, from both a company’s and their customers’ perspective, will be in a state of flux sooner rather than later. Cybersecurity is no longer an accessory — it should now be front-and-center and instrumental to all reputations involved and will become a driver in net profitability for product/service performance metrics and will be a new directive that influences a company’s brand value. Customers — both businesses and consumers — will become cognizant of the essentiality and features of state-of-the-art cybersecurity measures which will translate to a mandatory check-box on the short list. This cognizance will manifest from either, hopefully, insight or, unfortunately, hindsight. The rules of the game have changed and institutionalizing cybersecurity will soon be intuited as a first-mover, strategic advantage to leapfrog the industry totem in lieu of tactically being first to market with the next product cycle — the tortoise will steamroll the hare. This shift from tactical to strategic thinking will happen as more people and organizations learn that abstract threats in cyberspace have consequences even more crippling than primeval, visceral threats. All first-tier military forces know this; cyberspace has become the fifth dimension of modern warfare: land, air, sea, space, and now cyberspace. And that is up next.
Who are the Sources of Cyberterrorism?
In today’s world, state-of-the-art cyberterrorism is created and funded by multiple operators at the nation-state level executed either by a specialized branch(s) of the state’s military or anonymously channeled through proxies and can only be combated by very sophisticated cybersecurity firms that must perform like seasoned, cardiac surgery teams. Just like in the real-world you have Virus Hunters of the CDC (Center for Disease Control) hunting the Ebola virus and Lassa fever, in cyberspace there are virus hunters too. At the cutting edge, this is the way you need to visualize it: there are teams of specialists from artificial intelligence (AI), manifold software sub-disciplines all the way down to “at the metal” or root-level machine language, hardware, networks and communication protocols and, with growing frequency, old-school intelligence officers addressing espionage and/or sabotage — all of which must orchestrate harmoniously. Simply: forensic and hunting skills on multiple levels are teamed with experts in many technical disciplines and they have to perform on the clock and in sync.
As the adversaries’ tactics, techniques, and procedures (TTPs) change, so must the defenders’ approach; just as a biological immune system’s antibodies continuously evolve in lockstep with bacterial mutation, so does a cyberterrorist’s tradecraft. New species of threats emerge behind the shadows at any time. This is a very fluid dynamic; you cannot fight today’s war with yesterday’s weapons and tactics, it is a well camouflaged moving target. And it is rapid change that makes any prediction treacherous and borderline foolhardy; just like predicting a hurricane’s path 5 days out is much less certain than 2 days out, this same concept of a cone of uncertainty is front-and-center in cyberterrorism. From the C-suite perspective, it is never going to be a problem that is “handled”, the Red Queen is alive and well, locked and loaded. Only great “employee hygiene” of network access, incessant vigilance, state-of-the-art tools, and 24/7 learning are viable countermeasures.
Next, watch the short video Stuxnet: Anatomy of a Computer Virus. Following the video is a briefing on the major cyberwarfare nation-state programs.
There are five countries that have well-documented and formidable offensive cyberwarfare capabilities: the United States, Russia, China, Iran, and North Korea. Understand that there are many other countries invested in cyberweapon development along with thousands of small to medium non-state actor groups and networks and tens of thousands more “hacktivists wearing black hoodies with a laptop at Starbucks.” Very powerfulweaponized malware is available through open source along with tutorials on how to build your own lethal cyberweapon. What is in the public domain today is more powerful than what was a state-of-the-art, top-secret, skunkworks cyberweapon in yesteryear.
China
For an overview of China’s major targets, see this infographic:
Infographic of China’s Threat to Multiple Global Vertical Business Sectors(CrowdStrike) (2015) (pdf)
China’s capabilities: [ The Rand Corporation, 2015, The US-CHINA Military Scorecard: Forces, Geography and the Evolving Balance of Power 1996–2017, pp. 259–284 (pdf) | Jamestown Foundation | Washington Free Beacon | The Diplomat | Tri Pro Sec (pdf) ]
A recent example of China’s offensive capabilities:
The first of the breaches attributed to China-based actors was announced by healthcare provider Anthem in February 2015; it reportedly resulted in the acquisition of customer names, Social Security numbers, physical and email addresses, and income data for between 37.5 and 78.8 million customers. Two other U.S. healthcare providers, Premera and CareFirst (both under the BlueCross/BlueShield umbrella along with Anthem), followed suit in March and May, respectively. Premera reported a PII (ed. “personally identifiable information”) breach of up to 11 million of its customers, while CareFirst put the number around 1.1 million. All told, these healthcare breaches resulted in the compromise of anywhere from approximately 50 to 80 million Americans.
(Source: CrowdStrike 2015 Global Threat Report, p. 7 (register to download (pdf))
A snapshot of the Chinese philosophy of cyberwarfare and its asymmetric nature between offense and defense — defense is very difficult to flawlessly execute 24/7:
Although Chinese authors emphasize the importance of defense, they also see cyber warfare as inherently offense-dominant:
“Networks in integrated-whole terms have the features of susceptibility to attack and difficulty of defense, and this asymmetric quality of network attack and network defense is prominent.” [from 战略学 (The Science of Military Strategy), 3rd ed., 2013, pp. 192–193]
(Source: The Rand Corporation, 2015, Scorecard 9: U.S. and Chinese Cyberwarfare Capabilities, (p. 273) (pdf))
As supply chains become more complex, another weakness to exploit is computer hardware manufactured in China (or elsewhere) that can have malware designed into the hardware (firmware) itself and is then sold to military and civilian customers in the US. “Malware Inside” is not far-fetched speculative theory, either. When malware is “baked in the cake” it takes cybersecurity to a different level:
The Chinese could manufacture a corrupted device and find some way of getting it purchased and inserted into the SIPRNet [ed. Secure Internet Protocol Router Network]. When triggered, the device would carry out instructions designed to corrupt or disrupt SIPRNet operations. Concern about this possibility within the cyber defense community has resulted in increased scrutiny of DoD purchases.
and in footnote 12 on the same page:
In early July 2011, Greg Shaffer, acting Deputy Under Secretary of Homeland Security, was asked whether any software or hardware components embedded with security risks had been installed. He replied, “I am aware that there have been instances where that has happened.”
(Source: The Rand Corporation, 2015, Scorecard 9: U.S. and Chinese Cyberwarfare Capabilities, (p. 265) (pdf))
More from the National Security Cyberspace Institute, 2011, “Software (In-)Security”, (pdf)
Iran
Iran’s capabilities: [ U.S. Army War College | Washington Free Beacon|Foreign Affairs ]
After the use of Stuxnet on Iran, Iran effectively retaliated with “Operation Cleaver”. The report on how Iran stole thousands of credentials of key personnel and data in many industries is documented in this video and is well worth watching in order to quell erroneous pre-conceived notions of cyberterrorism and cybersecurity. Find out what it realistically means to be at the edge of the performance envelope in this discipline:
In-depth background report for this video: Iran’s Operation Clever (Cylance)
A continuation on the train of thought of sophisticated cybersecurity in action in the real-world is Cylance’s efforts on large scale attacks on Japan’s infrastructure from 2010 to 2016:
The group has already compromised a wide breadth of victims across the following industry verticals: electricity generation, oil and natural gas, finance, transportation, and construction. SPEAR’s current research indicates the group’s present focus has shifted to specifically and exclusively target Japanese companies or Japanese subdivisions of larger foreign organizations, including a major Japanese oil and gas company, a Japanese subsidiary of a South Korean electric utility, and a major Japanese automaker.
(Source: Cylance: Operation Duststorm)
To be clear, these attacks are not in reference to Iran; the attacker(s) is not referenced.
Russia
Russia’s capabilities: [ Militaire Spectator 2016 | Defense Tech | RSA Conference Europe 2013, William Hagestad II, Comparative Study between China, Russia and Iran (pdf) ]
Application of Russian cyberwarfare in the Ukraine:
Much of the clandestine cyber conflict in Ukraine focused on directing public sentiment through the application of pressure to centers of gravity. Some of those centers of gravity have been broadly identified through current targeting actions as the military, energy sectors, media, government, and and non-governmental organizations. Looking specifically at the critical infrastructure center of gravity, it is easy to identify a persistent pattern in targeting within the energy sector. The Ukrainian energy sector was targeted as early as May 2014 when BlackEnergy malware was discovered on power company networks.
The totality of these events, from May to the present, exemplifies how hybrid conflicts are conducted across the physical and information battlespace, also referred to as “the fifth domain”. A force able to cause physical effects by leveraging the fifth domain is a force to be reckoned with.
(Source: CrowdStrike 2015 Global Threat Report, pp. 27–28 (register to download (pdf))
North Korea
North Korea’s capabilities: [ Center for Strategic & International Studies |University of Washington (Jackson School of International Studies)| U.S. Naval Postgraduate School | Security Affairs ]
Recent North Korean cyber attacks show that only understanding North Korea in light of its conventional military confrontations with democratic countries is outdated. The characteristics of cyberspace and cyber warfare have allowed North Korea to pay more attention to developing and exerting its cyber capabilities. In other words, North Korea benefits from the low cost of entry, anonymity, and the plausible deniability that cyberspace offers. At the same time, the international community has not monitored the development of North Korea cyber capability and it has not imposed any sanctions against North Korea for its cyber activities. This is largely due to the difficulty attributing attacks to North Korea. North Korea’s successful cyber strategy indicates that it can achieve its strategy pillars without a threat of increased economic sanctions through developing its cyber capabilities, instead of solely focusing on the conventional weapons.
(Source: Donghui Park, University of Washington, June 28, 2016, “North Korea Cyber Attacks: A New Asymmetrical Military Strategy”)
From 2013–2015, the Director of National Intelligence named the cyber threat as the number one strategic threat to the United States, placing it ahead of terrorism for the first time since the attacks of September 11, 2001. Potential state and non-state adversaries conduct malicious cyber activities against U.S. interests globally and in a manner intended to test the limits of what the United States and the international community will tolerate. Actors may penetrate U.S. networks and systems for a variety of reasons, such as to steal intellectual property, disrupt an organization’s operations for activist purposes, or to conduct disruptive and destructive attacks to achieve military objectives.
Potential adversaries have invested significantly in cyber as it provides them with a viable, plausibly deniable capability to target the U.S. homeland and damage U.S. interests. Russia and China have developed advanced cyber capabilities and strategies. Russian actors are stealthy in their cyber tradecraft and their intentions are sometimes difficult to discern. China steals intellectual property (IP) from global businesses to benefit Chinese companies and undercut U.S. competitiveness. While Iran and North Korea have less developed cyber capabilities, they have displayed an overt level of hostile intent towards the United States and U.S. interests in cyberspace.
(Source: Department of Defense Cyber Strategy, April 2015, “II. Strategic Contexts”, p.9, (pdf))
Relevant background:
CBS 60 Minutes segment on North Korea’s cyber attack on Sony
Sunday Guardian (India): North Korea expands cyberterrorism forces to 5900
Challenges Moving Forward
Modern computers and their networks impose an inherent, Siamese twins relationship between functionality and vulnerability:
First, the challenges in implementing effective cybersecurity are technical and involve attributes of systems that are integral to their design. Modern military systems (and information technology systems) are so complex that only specialists can understand the detailed operations of the protocols, identify critical vulnerabilities, and understand how to address these vulnerabilities without compromising functionality. Many of these details are specific to each military system, and therefore the technical knowledge is confined to a very limited number of experts.
Second, functionality and cybersecurity are intertwined. Quite a number of cyber vulnerabilities are the result of features deliberately designed into systems. That is not to say that engineers aim to make vulnerable systems, but during design, engineers make trades between functionality and security and are willing to accept certain levels of vulnerabilities in order to achieve some functionality, often knowingly, and sometimes unknowingly. One example is that desktop computer operating systems permit other computers to download and run executable code from World Wide Web sites. Much of the functionality of the World Wide Web comes from this ability, which allows for a powerful range of applications. But it also permits the loading of malware from malevolent actors. Much of the commercial world is so driven by introducing new functionality that security is a lesser priority, and, when addressed, security is introduced by overlays on an insecure design rather than by an inherently secure design.
(Source: RAND Corporation, 2015, Improving the Cybersecurity of US Air Force Military Systems Throughout Their Lifecycles, “Attributes of Cybersecurity That Inform How It Needs to Be Managed”, p. 6)
Modern, integrated supply chains harbor unique vulnerabilities:
Traditional security controls used in a layered security strategy have not fully protected transportation and logistics organizations and have proven to be static in their defense. They lack the adaptability to proactively defend against the speed and sophistication of new advanced malware, insider and zero-day threats, and the use of Tor and anonymous proxies to hide and anonymize malicious network activity.
(Source: Norse Corporation, 2014, “Reducing the Risk of Cyber Attacks to Transportation & Logistics Organizations with Live Attack Intelligence” (pdf))
“Computer system” cannot be restricted to purely digital environments for information processing and repositories for work-product and intellectual property. Recall how Stuxnet was able to destroy the Iranian centrifuges by taking over the automated mechanical and electrical systems that control the nuclear reactor. These are called industrial control systems (ICS) andthey are everywhere in modern societies because of the improved reliability and reduced costs from automation and automation means software and software has a fluorescent red dot on its back — ICS-specific attacks are a relatively soft target due to neglect because they are not considered “cyber” and are a major objective of cyberterrorism and cyberwarfare at the state-of-the-art level of the offensive-mindset.
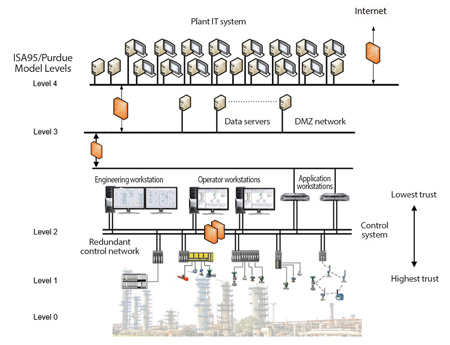
The trust levels of Level 2 workstations and servers are lower than controller-level and field devices for three reasons:
They run commercial operating systems and software (e.g., SQL database software) with vulnerabilities that are continuously being discovered and exploited.
They have a better chance of being infected or compromised, because they can be accessed by Level 3.
They have users who may not always follow policies and procedures — some may plug in nonverified USB sticks, plug in their smartphones to charge, or bring in their own software that has not been tested to operate correctly with the ICS.
The trust levels associated with field devices, controller-level devices, and workstations are inherent to most control systems. Understanding them and maintaining separation/isolation between them is a responsibility that is normally not present in IT systems.
(Source: International Society of Automation, Lee Neitzel and Bob Huba, 2014, “Top ten differences between ICS and IT cybersecurity”)
Attacks of this nature are going hockey stick:
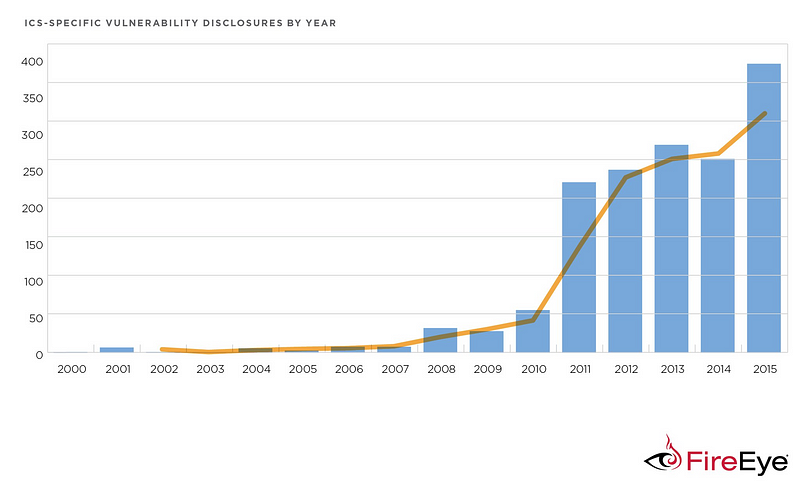
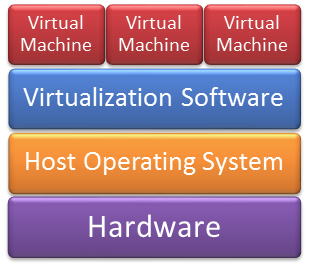
Legacy computer hardware and software architectures like Intel x86 chip sets and the Microsoft Windows operating system kernel were never intended for today’s networked world. Also, the recent trend of virtual machine architectures that are becoming extremely popular is a new vulnerability opportunity:
Over the years, an arms race has been raging between system designers and researchers driving down to the silicon chips that support the boot process, exposing previously unknown flaws in software that we rely on every day. This leads to enhanced protections, and in some cases, wily attackers can use the flaws to compromise systems at a very low level.
Virtual Machine computing is another area of intense research. In the last year, it became apparent here, too, that low-level drivers and code to support antiquated devices could diminish the security of the overall system. With these research stories slowly percolating into the mainstream media, it is important to keep an eye on novel research that may lead to critical exposures in the future.
(Source: CrowdStrike 2015 Global Threat Report, p. 72 (register to download (pdf))
Data breeches and IP theft, because they are asymptomatic, can persist for a long time before discovery, if they are discovered at all:
Numbers always tell a story, but it’s the interpretation of those numbers that holds the real value. The median number of days an organization was compromised in 2015 before the organization discovered the breach (or was notified about the breach) was 146. This continues a positive improvement since we first measured 416 days in 2012. Additionally, the median number was 205 days in 2014, which means we witnessed a drop of more than 50 days in 2015! Obviously, as an industry, we are getting better at detecting breaches.
(Source: Mandiant Consulting (FireEye, Inc.), February 2016, M-Trends 2016, p.4 (register to download (pdf))
Back-of-the-napkin calculation shows significant cost saving by outsourcing IT to the cloud; everyone is doing it from two-person startups to Fortune 500 companies — why not? However, the sea-change migration to the cloud has created new vulnerabilities that have proven difficult to detect. It is not that cloud computing is necessarily worse than keeping IT “in-house”, it is thatsecuring your intellectual property and work-product is outsourced along with your data so that a new level of coordination, implementation, and validation of security is in order and owning the responsibility is currently not up to the task:
The most damaging outsourced service provider abuses we saw this past year were related to the IT outsourcing (ITO) industry. By working with victim organizations and their outsourced IT service providers, we have identified multiple advanced attack groups that have persisted across various ITO infrastructures for more than at least two years — and five years in one instance. The attackers were maintaining persistence to the ITOs and leveraging them for unrestrained access into the targeted companies that employ the outsourced services. The goals of the attackers varied for each of the end client victims, but the actors were primarily focused on stealing sensitive data from those organizations while maintaining access to the ITO infrastructure for additional campaigns targeting other companies.
(Source: Mandiant Consulting (FireEye, Inc.), February 2016, M-Trends 2016, p.24 (register to download (pdf))
In the cloud, how sure are you that your IP is safe? At the present time, this is a question that cannot be answered with any acceptable degree of confidence — either technically or legally — simply because it is unknown. The much more haunting, perplexing question is: is it knowable, ever? The Red Queen problem comes to roost here as a permanent, intractable fixture: the combination of technology, complexity, and the sum of human plus machinic cognitive powers is akin to a mirage that topologically features fatter and longer tails over time — it harbors hidden risks that elude identification, quantification and neutralization. The fact of the matter is that no matter how much “somebody” (machine + human) knows or claims to know, the knowable + unknowable is always a superset of that and — most critically — the Red Queen’s niche exists at the extreme margin of the knowable, perpetually just out of the desperate grasp of the most competent defensive measures. All that can ever be done is to deploy the best defense possible, there is no such thing as “good enough.” Arriving at an accurate measure or even definition of “cost effective” is a slippery slope at best.
How Vulnerable is the US Power Grid?: Assessing U.S. Power Grid Vulnerability is Not a Black or White Question
Cyberterrorism and cybersecurity is a very fluid battlespace. Finding credible information that provides an infallible assessment on the vulnerability of the US power grid is not available and quite possibly is unknown because ofunknown unknowns for all parties involved — offensively or defensively. The video provides a conversation between Richard Ward, Senior Manager of National Security Policy for the Edison Electric Institute and Norm Laudermilch, COO of Invincea, a cybersecurity firm:
http://www.youtube.com/watch?v=p_CKayMBYV8
Now the US military’s position:
“Yes, China and one or two others can shut down our power grids.”
Role of U.S. Cyber Command (NSA) in protecting 16 facets of critical infrastructure including the power grid, water, financial centers, and transportation.
Admiral Michael S. Rogers, U.S. Navy, Commander, U.S. Cyber Command, Director, National Security Agency/Chief, Central Security Service [Source:RSA Conference 2016, (video)] [Source of quote: Admiral Michael Rogers inConstruction Week, 2015, re: Cylance]
The Future of Cybersecurity
Throughout this intelligence briefing an emphasis has been placed on the dynamics of the battlespace between offense and defense; this is the realm of the Red Queen problem which is always in flux and never gets old. As more technology and more complexity is released into the digital ecosystem, new parasites and predators emerge and enjoy a field day from the new, unintended terrain featuring awesome new niches of exposed, low-hanging fruit. In the blink of an eye, the cybersecurity you have may no longer be viable.
Artificial intelligence (AI) is the vanguard because of its ability to detect subtle new patterns of suspicious behaviors; it can detect a needle in the haystack of large data flows. The previous strategy of uploading new malware signatures or blacklists is outdated because the damage is already done; at the current state-of-the-art, new weapons are unique (“one-off”) creations that effortlessly swim through static, defensive nets. In other words, the old way of catching malware was based on the idea of detecting a signature structure of known malware; now it is based on what it does, particularly behavior patterns that are anomalous with normal data behavior relative to your indigenous environment. If something questionable is discovered, then quarantine or “sandbox” it before it causes harm. But theRed Queen never sleeps and neither does the offense: tens of thousands of people with offensive mindsets from all around the world are hard at work honing their hacking skills and developing more menacing cyberweapons to sidestep your best efforts. Your mission: prevent something that never existed before — a cadre of humans, no matter how smart, cannot do that.
http://www.youtube.com/watch?v=kao05ArIiok
Several cybersecurity companies are offering products based on AI technology which are showing a track record of success relative to previous approaches. Cylance, CrowdStrike, FireEye and Invincea were mentioned above and use machine learning techniques but there are many companies harvesting ideas from the AI corpus. For example, IBM’s Watson is now deployed in a cybersecurity capacity by being able to augment human intelligence via predictive analytics, a statistical approach crunching very large data sets looking for patterns. Cylance relied on machine learning in connecting the dots on attacks on Japan’s infrastructure that most likely would have gone unnoticed by humans alone.
One thing is certain: the future of cybersecurity and cyberterrorism at the highest level will not be incremental changes to present approaches. The level of complexity that computer science has taken us so far, from Alan Turing and John von Neumann to ARPANET to today — the internet + webet al — has now become complex enough to qualify as rudimentary models of biological function — and the diversity, quality and count of avant-gardebiological models from a panoply of sub-disciplines is legion. A quick study of biomimetics, for example, would provide copious templates for fortifying either offensive or defensive aims.
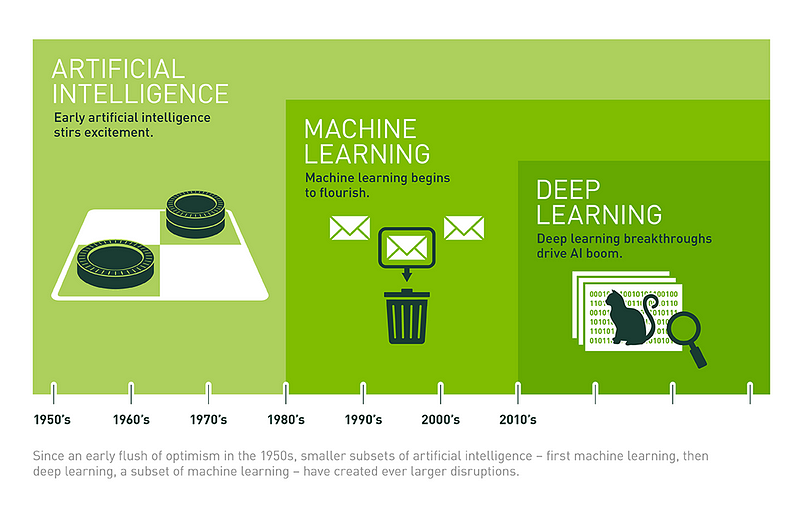
Deep learning, although considered a form of machine learning, uses a different approach algorithmically based on the old AI idea from the late 1950s of neural networks inspired by neuroscience. This approach has been resurrected because powerful graphic processing units (GPU) hardware such as NVIDIA GPUs that were originally designed for rendering video images in gaming is remarkably well suited to neural net algorithms featuring many layers. The best known example of deep learning is Google’s DeepMind that defeated the world-champion human Go player recently; this approach will bear fruit for the next generation of cybersecurity. Deep Instinct, an Israeli startup in 2015, is already taking this approach. Leapfrogging will favor those who conceptualize outside-the-box, not those hamstrung by minutiae or basking in the inertia of past success. The bold will be richly rewarded because boldness, in biology, is tantamount to a successful mutation which amplifies fitness — and it is fitness that equals scoreboard. What you want to do is pull a black swan out of the hat out of the blue because it is precisely that that rattles the cage. In any case, whichever side of the battlespace you fancy, plan accordingly and avoid overconfidence and hubris at all costs. Remember, you are only as good as your last kill — or save — whichever it may be.
What has not been aired is the use of AI to build the next generation of cyberweapons. There is a lot of discussion about AI from the cybersecurity side of the equation but that only tells half the story. Van Valen’s Red Queen hypothesis foretells a simple universal truth: what is good for the goose is good for the gander. If a turtle develops a thicker shell, a hawk develops sharper claws. If not, then extinction draws nigh. Given the preponderance of massive and cheap computer power available as hired guns on the cloud whilst turnkey, general-purpose AI toolsets abound, expect new cyberweapons spawned from the AI crucible. Brave New World, indeed.
Ramifications
The very definition of war and peace is challenged when it becomes increasingly difficult to tell the difference between cyberterrorism and cyberwarfare conducted by the major state actors or, soon, easy access by small, well-funded hacktivists to open-source cyber assets featuring upgraded, lethal payloads. Caught in the crosshairs of this nebulous gray zone between act of war and egregious theft is your company’s future prospects. This intelligence briefing has made it clear beyond the shadow of a doubt that cyberterrorism is on the short list of the greatest problems facing the stability of modern societies in more dimensions than one and that time is not in the favor of peaceful outcomes.
Prudent Actions to Strongly Consider
If you are a CEO, cyberterrorism is a threat that showcases both danger and opportunity: your business is imperiled while at the same time if you act swiftly it can be a strategic means to climb the ladder of visibility in your industry in a positive as opposed to a negative (victimized) sense. If you are an individual, understand that your way of life could be severely impaired if a massive, coordinated attack is invoked. This is no longer merely a theoretical concern or fiction because the tipping point is now in the rearview mirror: the proliferation of offensive actors on a global scale empowered by the escalation of extensible and lethal cyberweapons just a click away quietly has become the new normal. Ignore Darwin and the Red Queen at your own peril.
Notes
*Conflict of Interest: none
**The legal profession, because it is a repository of IP and confidential information, has become a target itself. (Source: Information Week (Dark Reading), “Legal Sector’s Threat Intel-Sharing Group Grows”)

If you are decision maker in business feel free to contact me about cybersecurity.
Prepared by: James Autio
doctorgo@gmail.com
___
http://medium.com/deepconnections/prevailing-gray-swans-4-august-19-2016-c2f2023ef72c#.z9y1gt2b8

